How Poor Risk Management Is Hurting Your Program
Project Risk Coach
JANUARY 24, 2022
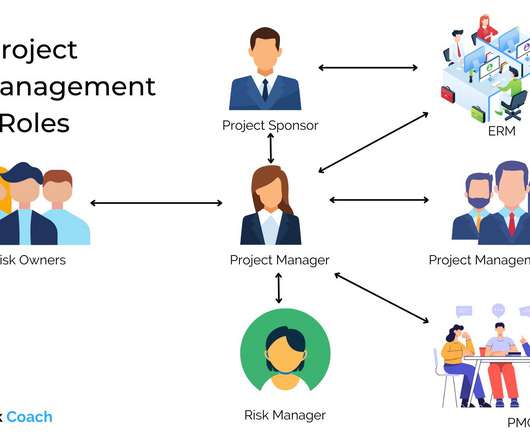
Poor risk management is costly. Let's look at the cost of poor risk management through the example of Tom Whitley. The Risk Management Mistakes of Tom Whitley The Star Mutual Insurance Company (SMIC) hired Tom Whitley as a project manager to manage information technology projects. But, it doesn't have to be that way.



























Let's personalize your content