How To Ensure Data Privacy in Customer Relationship Management
Binfire
FEBRUARY 19, 2024
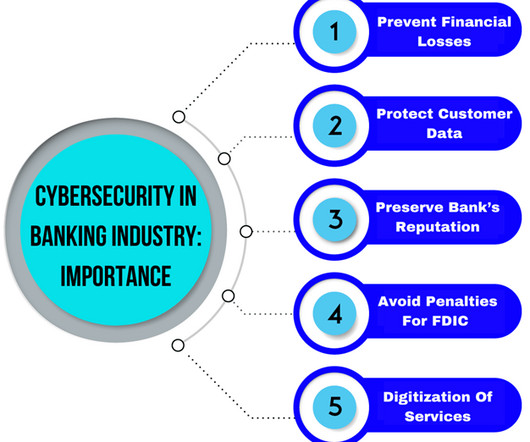
Businesses of all sizes are investing massively in data management and leveraging its potential to outpace their rivals. However, cyber crimes have become the new normal, ravaging the digital space and causing businesses to fall into ruins. Everyone is talking about it. What does it mean? Keep reading to learn more.











































Let's personalize your content