How to Secure Resources for Your Projects
Rebel’s Guide to PM
APRIL 27, 2023
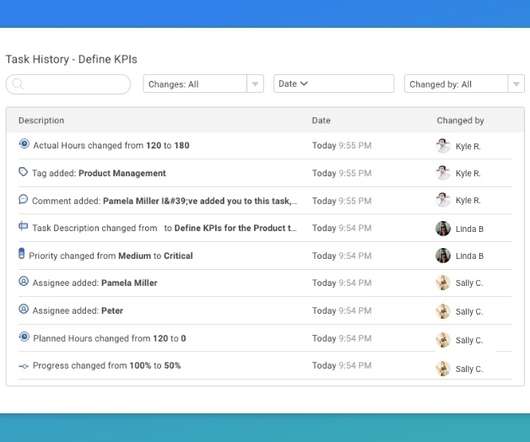
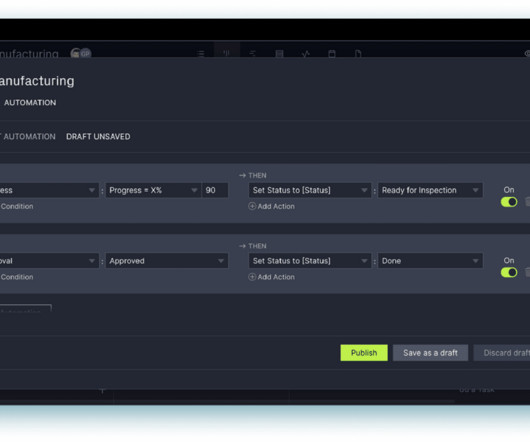
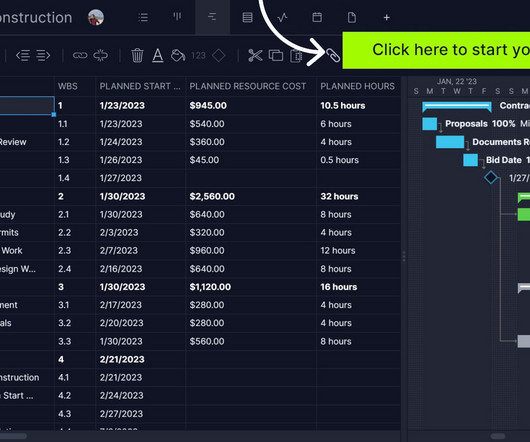
If you have secured time from an individual, look across all your projects to see how you can best use it, especially if there are lulls in the upcoming work. In some situations – for example where your organization does not yet have a mature approach to managing projects – the onus falls to you to ensure you secure support for your work.











































Let's personalize your content