Top 5 Best Slack Alternatives
Productivity Land
FEBRUARY 26, 2024
Connect the best productivity apps in one place, and do not worry about data security. The Slack Enterprise Key Management technology-enhanced collaboration security. Secured file-sharing of different formats and sizes facilitates the work process. 5 Twake Twake is an open-source tool that is simple and secure to use.



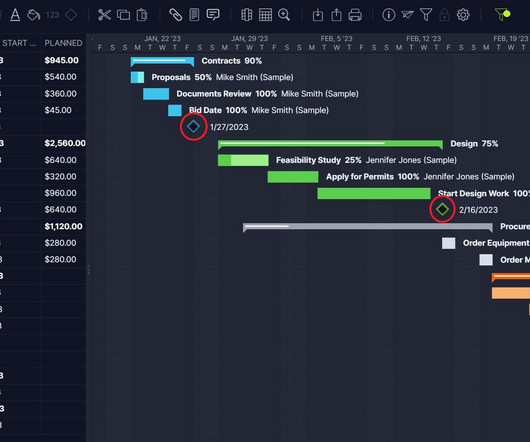

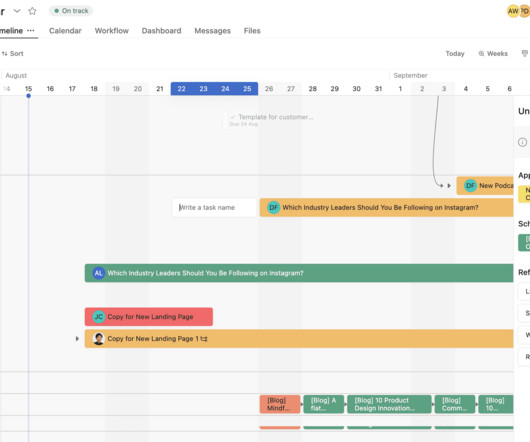

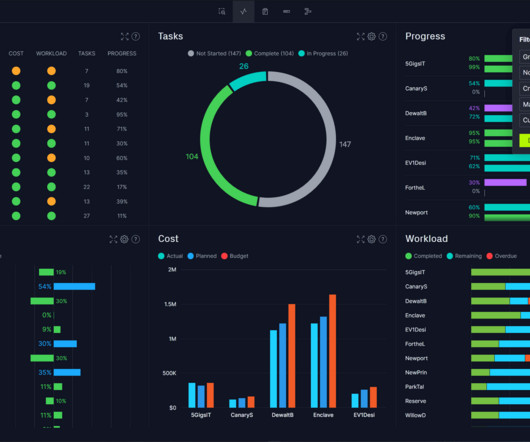






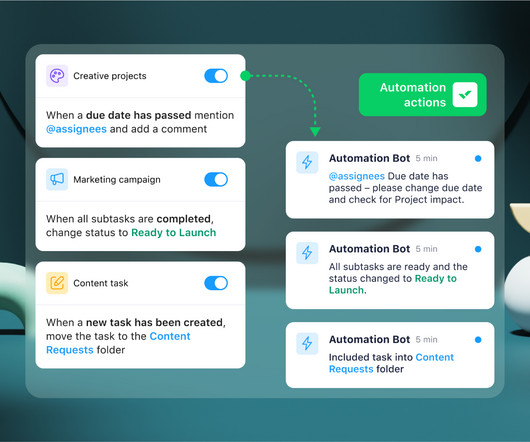











Let's personalize your content