Access Control in Physical Security: The Key to Comprehensive Protection
Productivity Land
DECEMBER 12, 2023
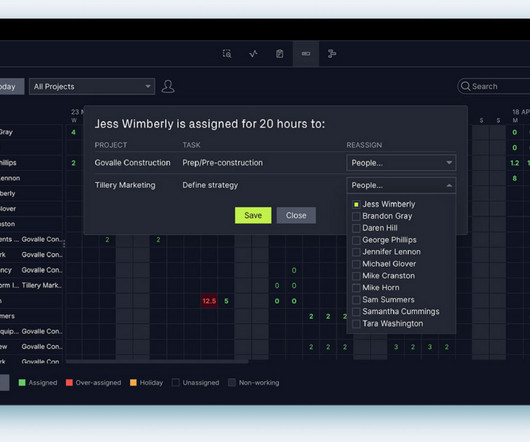
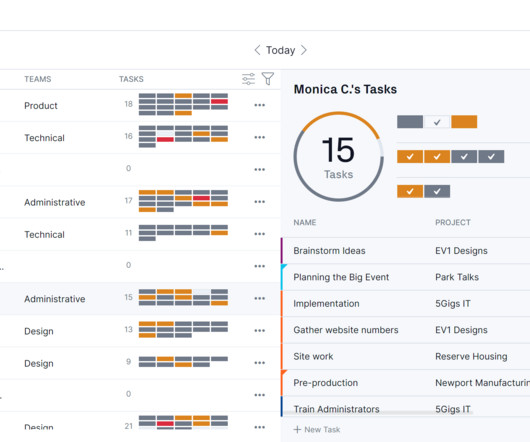
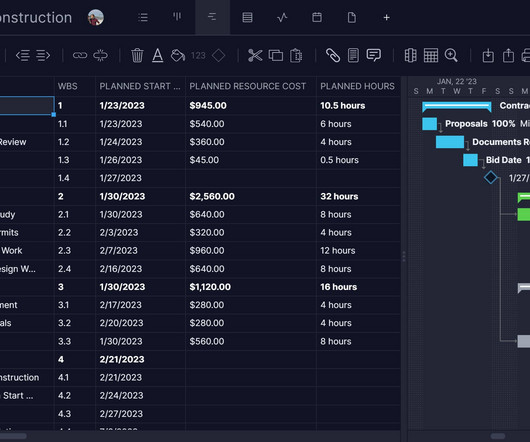
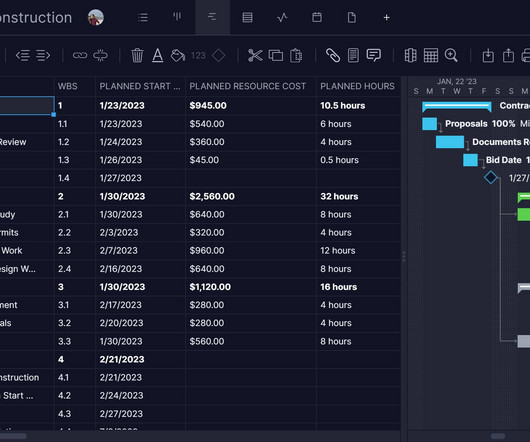
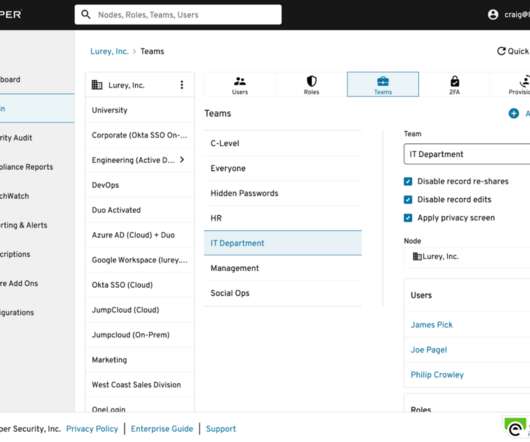
In the realm of physical security, access control systems play a pivotal role. This is where companies like Genetec, a leader in security solutions, come into the picture, offering state-of-the-art access control systems that are reliable and integrate seamlessly with other security technologies.
































Let's personalize your content